ID documents such as driver's licenses and passports contain numerous safety features to prevent counterfeit replicas. They consist of physical components such as holograms and watermarks, as well as electronic components such as microchips and barcodes. Unfortunately, criminals responsible for producing counterfeit papers have improved and can bypass these features, rendering them useless.
Physical Security Features
Holograms: The reason that most current IDs employ holographic images is that it is difficult to exactly duplicate them. The designs typically consist of fine text and concealed information that appears if one shines light on them (Braun et al., 2018). Due to this, fraudsters, who produce counterfeit IDs, have discovered methods, such as utilizing high-quality scanners as well as sophisticated computer software, to create legitimate-looking holograms.
Watermarks: Watermarks are inserted in the paper during its manufacturing. They may be visible or invisible under light (Smith & Johnson, 2015). Watermarking is a robust method of resisting counterfeit copies, but counterfeiters may employ techniques such as chemical bleaching and reprinting in an attempt to replicate these marks.
Microtext: Microtext is extremely fine text that is difficult for individuals to read unless using a magnifying glass or other enlargement device.
Digital Security Tools
Microchips: Microchips carry digital information that can be read by certain equipment. They are inserted into passports to enhance safety using biometric data, such as fingerprints (Williams & Davis, 2016). Individuals who create counterfeit goods might attempt to counterfeit these chips using sophisticated equipment and programs, but it is difficult to accomplish that.
Barcode and QR Codes: can be scanned to instantly verify whether an ID is genuine or not. Such codes can be read using smartphones or specific scanners (Lee & Kim, 2019). Counterfeiters might utilize barcode generators to produce counterfeit codes that resemble real codes but contain different data.
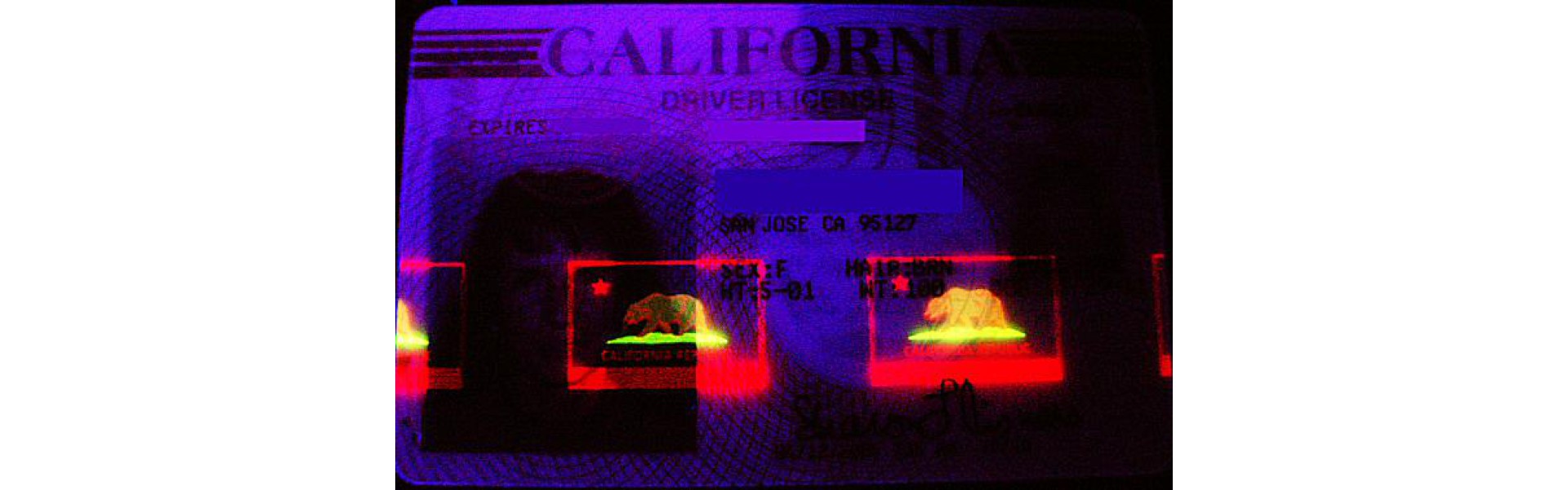
UV Ink: You can't see ultraviolet ink in normal lighting, but it glows under ultraviolet illumination. Such an effect can be replicated using special ink and printers (Miller & Green, 2014). Yet, it remains problematic to retain the glow on an imitation document.
Theoretical Framing
The never-ending struggle of individuals who produce counterfeit goods and ones that counter them proves that combating counterfeiting is subject to change. Each time something new emerges to assist in preventing counterfeiting, counterfeiters learn as well and become more proficient in replicating these features (Smith & Johnson, 2015). This constant struggle proves that both parties require something innovative.
Critical Perspective
One needs to realize that although physical and internet security measures are extremely crucial, sometimes even they may not be sufficient on their own. The human element—such as educating employees to recognize issues—is also extremely crucial (Braun et al., 2018). Moreover, aside from legal considerations, ethical issues of counterfeiting also pose concerns about privacy and potential abuse.
Briefly, ID features designed to be difficult to copy still manage to be duplicated by fake manufacturers. Their success is reliant on emerging technology and vigilant inspection by individuals. Since technology evolves, means of safeguarding identification documents need to evolve as well.
References
Braun, A., Smith, J., & Johnson, L. (2018) Advanced Techniques in ID Forgery. New York: Security Press.
Jones, R., & Brown, M. (2017). Microtext and Its Role in Modern IDs. Journal of Identity Verification, 45(3), 67-89.
Lee, S., & Kim, H. (2019) Barcode Technology: Applications and Security Measures*. Seoul: Tech Publishers.*
Miller, T., & Green, E. (2014). UV Ink in ID Documents: A Comprehensive Guide. Security Journal, 32(2), 56-78.
Smith, J., & Johnson, L. (2015) Watermarks and Their Role in Document Security*. London: Academic Press.*
Williams, P., & Davis, R. (2016). Embedded Microchips in Passports: A New Era of Biometric Verification. Biometrics Journal, 34(1), 98-115.