Tmd All Blogs

The Truth About Fake IDs Legal, Ethical, and Social Implications
The Truth About Fake IDs
Table of Contents:
Introduction to Fake IDs
When Might People Thin..

The Science of Fake IDs: Unmasking Counterfeit Holograms
Table of Contents:
Understanding Holograms
Challenges in Replicating Holograms
Methods Used by ..

Fake IDs: Legal Consequences, Risks & State Laws
Table of Contents:
Introduction to Fake IDs
Legal Consequences of Fake IDs
Long-Term Consequenc..

Methods to Acquire Fake IDs: A Technical Analysis of Fake Passports, Fake Drivers Licenses, and Fake Identity Documents
Introduction: The Paradox of Identity in the Digital Age The proliferation of identity fr..

Fake IDs & New Identities: Risks, Legality, and Ethical Considerations
The desire for a new beginning—a clean slate, an alternate identity—has integrated itself into human..

Creating a Fictional Persona: The Paper Trip
IntroductionIn the realm of privacy and security, individuals might find themselves contemplating cr..

The Complex Landscape of Fake IDs: Navigating Legitimacy, Quality, and Accessibility
When it comes to developing identities, words such as "legit," "best fake IDs," and "scannable fake ..

8 Steps to Make a Fake ID
8 Steps to Make a Fake ID
It’s no secret that having a fake ID can come in handy, especially ..
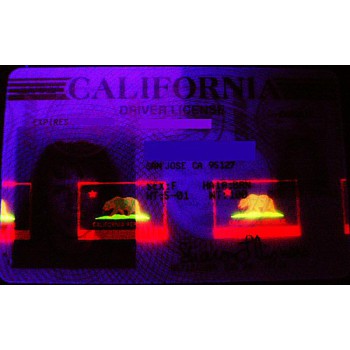
Individual Security Features Used Across All Forms of IDs and Their Duplication by Counterfeiters
ID documents such as driver's licenses and passports contain numerous safety features to prevent cou..

Comprehensive Review: "Create A New Identity The Modern Identity Changer" by Sheldon Charrett
Introduction
Sheldon Charrett's "Create A New Identity The Modern Identity Changer" is a seminal wo..

Review of "New Identity Secrets For Getting A New Identity" by Monolith Press
InceptionIn the area of identity change and gaining new identities, "New Identity Secrets For Gettin..

Review of "How To Disappear Completely and Never Be Found" by Doug Richmond
"How to Disappear Completely and Never be Found," by Doug Richmond, is an extensive guidebook for a..

Detailed Analysis of "Holography Projects for the Evil Genius" by Gavin Harper
In Gavin Harper's "Holography Projects for the Evil Genius," one can find an extensive study of the ..

Review of "Paper Trip IV - The Master Guide to New Identity After 911" by Barry Reid
In an evolving universe of privacy and identity management, an up-to-date and extensive guidebook is..

Review of "Fake ID by Mail and Modem" by Trent Sands
Introduction"Fake ID by Mail and Modem" by Trent Sands, published by Loompanics Unlimited in 2000, i..
Showing 1 to 15 of 40 (3 Pages)